





100% open source

Victory of Samothrace
Analyze network traffic to extract confidential information.
Wi-Fi
Lungo Motion Detector
Disable a motion detector remotely by exploiting an MQTT protocol flaw.
MQTT
Louvre Security System
Gain administrator access by exploiting a flaw in internal software.
UART
The Golden Scarab
Inspect inter-component communications and retrieve exchanged data.
Logic signals
Copernic Industries BBQ
You work for Copernic Industries and the CISO asks you to investigate a security flaw affecting the flagship BBQ product.
It seems your subcontractor has been compromised and a backdoor may be deeply installed in the product. You have one hour to investigate find the backdoor and attempt to neutralize it.
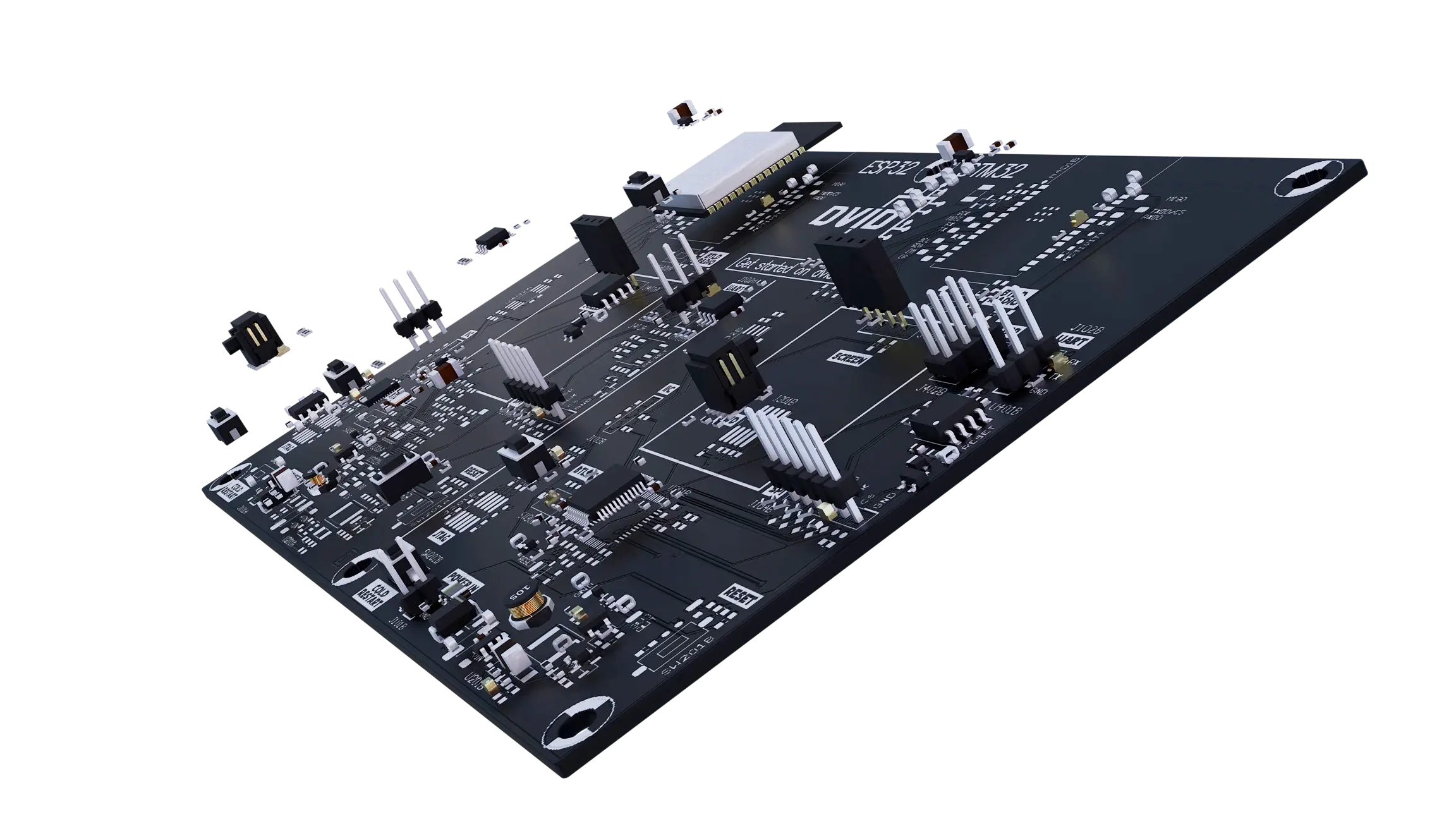
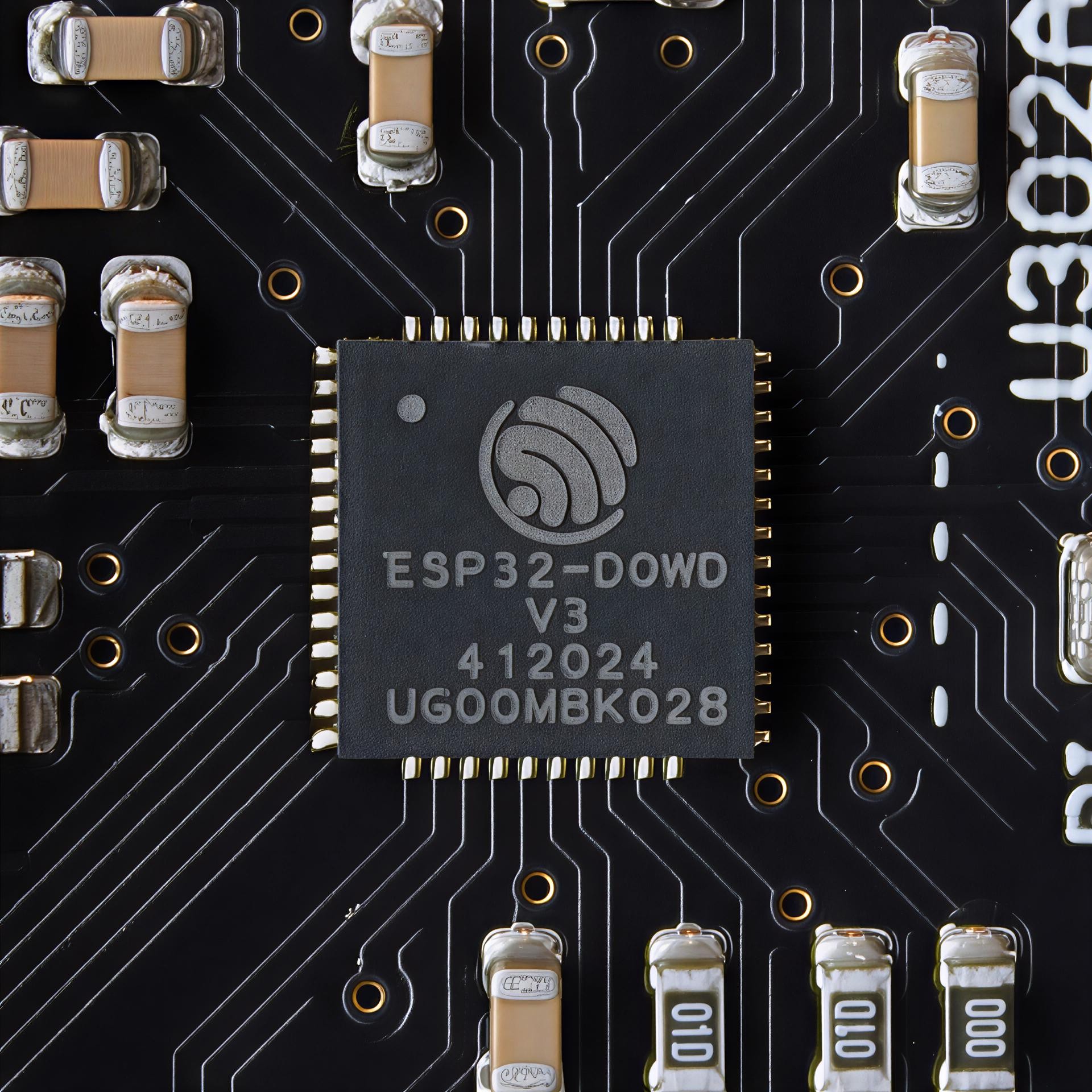
DVID/WOCSA Workshop
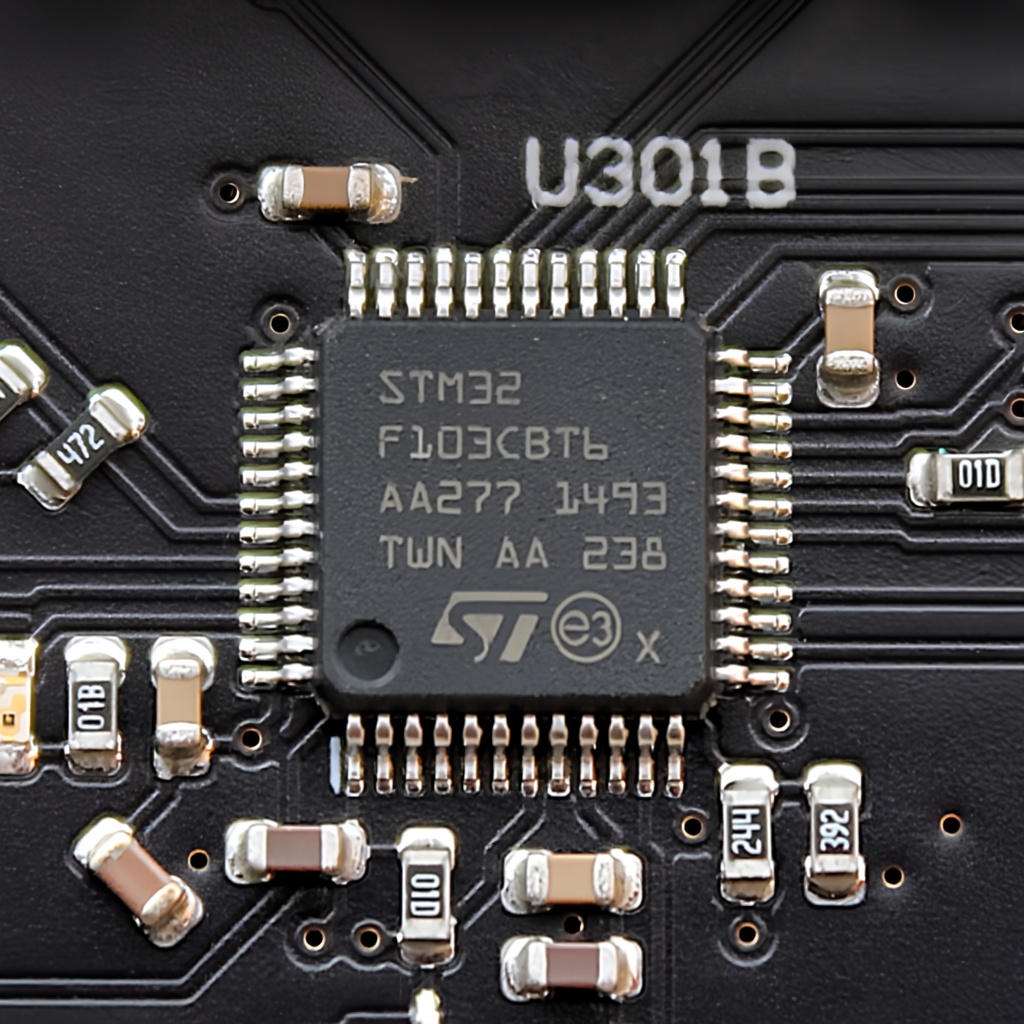
This workshop offers a hands-on introduction to exploiting UART ports on the DVID board, focusing on the STM32 side. Participants learn to correctly connect the UART port to the STM32F103 microcontroller, dump and analyze the firmware, observe its behavior in real-time, and extract artifacts or indicators useful for reverse engineering and threat intelligence.
